Extend the Power of Polarity
Polarity is an overlay on top of all your existing workflows and tools. You can also build on top of Polarity to extend the power of the platform. Explore available open source projects here:


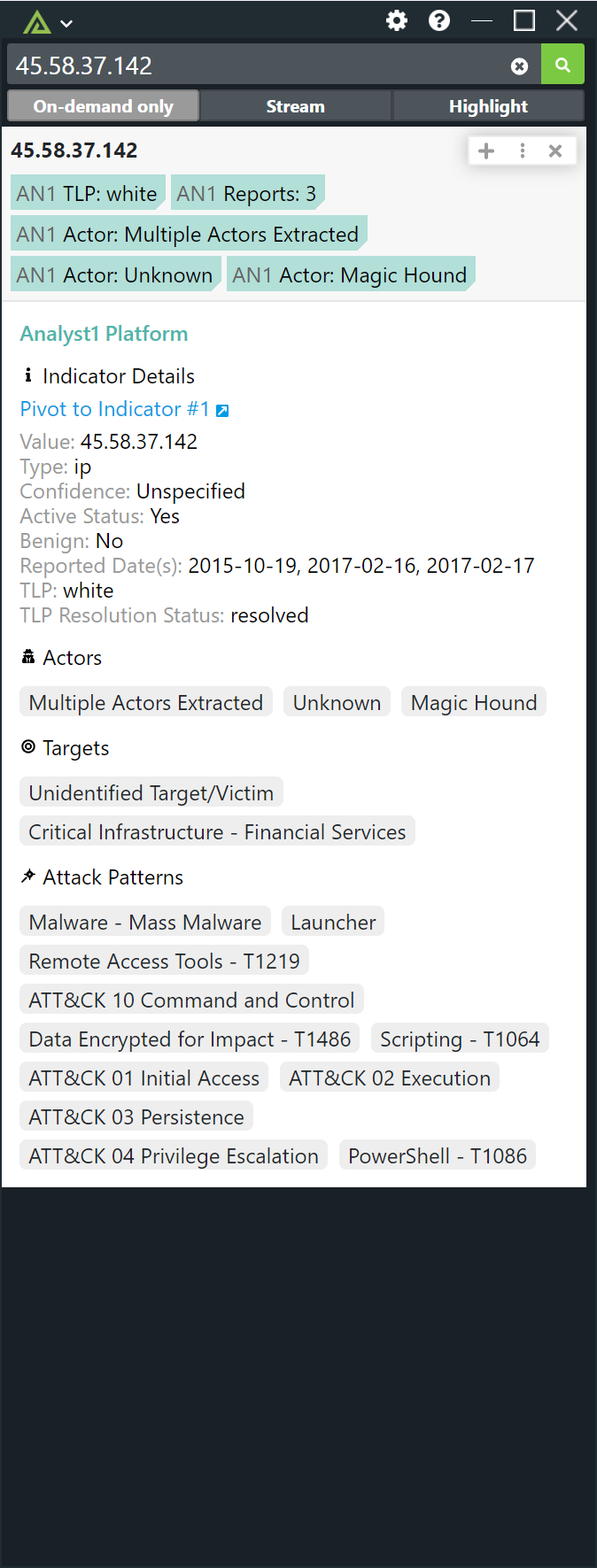
The Polarity <> Analyst1 integration allows Polarity to get quick identification of Indicators and CVEs associated to Actors, Malware, and MITRE ATT&CK from the Analyst1 platform. Analyst1 maintains a comprehensive threat intelligence archive from free, paid, and internal sources powered by NLP automation and analyst curation. Analyst1 provides total data provenance in control by the customer, greatly increasing the simplicity of access and depth of data available for Polarity’s augmented views to end users.
 Learn more
Learn more
The Polarity Azure ADFS Error Codes enables analysts to have information on what the error code is and how to resolve the error.
Learn moreOn-Demand integration which decodes Base64 and URL Encoded strings
Learn moreThe Polarity BinaryEdgeintegration allows for enrichment of IP's, Domains and E-mail addresses. Free accounts are limited to 250 queries per month. If you are using a free, account we highly recommend running this integration as On-Demand Only. Register for a free account at the URL below: [https://app.binaryedge.io/sign-up](https://app.binaryedge.io/sign-up "https://app.binaryedge.io/sign-up")
 Learn more
Learn more
Security Operations Incident Response Threat Hunting Pen Testing Network Engineering SIEM
Polarity's Chronicle Backstory integration allows automated queries to the Events, Assets, and IOC Details endpoints in Chronicle Backstory's API from the Polarity overlay window.
Learn moreThe Polarity Cisco Threat Response integration allows Polarity to search the Threat Response Enrich API to return information about various indicator types.
Learn moreThe Polarity-Cisco Umbrella (formerly known as OpenDNS) provides immediate awareness on domains. Enabling an analyst to quickly know if a domain is malicious benign or uncategorized, also categorizing the domain into content and security categories.
 Learn more
Learn more
The Polarity-Confluence integration benefits analysts by facilitating access to up-to-date information for any Space, Attachment, Page, or Blog associated with the connected Confluence account. Results are returned for any email address, domain name or IPv4/6 address mentioned in Confluence description.
 Learn more
Learn more
The Polarity Cortex XSOAR IOC Submission integration allows Polarity to search your instance of Cortex XSOAR to return found domains, IPs, hashes, and emails. The integration also allows you to Create and Delete Indicators and Incidents (IOCs) in bulk from Cortex XSOAR.
 Learn more
Learn more
CRITs is an open source malware and threat repository that leverages other open source software to create a unified tool for analysts and security experts engaged in threat defense.
Learn moreThe Polarity CRXcavator integration is an on-demand integration which provides risk information about third-party Chrome extensions based on the extension ID. The extension ID is a 32 character string made up of alphabetical letters. The integration will return risk information for the most recent version of the extension as well as information for the version of the extension with the maximum risk, and information for the version of the extension with the minimum risk. Finally, a risk history table is displayed which lets an analyst view the change in risk over time for the integration.
 Learn more
Learn more
CVE Search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and processing of CVEs.
Learn moreThe Polarity - Cyber Risk Analytics integration searches Cyber Risk Analytics for known breaches related to domains and emails on your screen.
Learn moreThe Polarity CyberReason integration allows Polarity to search CyberReason's API to return threat information on IP's, Domains and File Hashes.
Learn moreThe CyberSponse CyOPs platform is a holistic and enterprise built security orchestration and security automation workbench that empowers security operation teams.
Learn moreThe Polarity DarkOwl integration allows you to query various indicator types against DarkOwl Vision’s DARKINT data collection.
Learn moreThe Polarity-Dig integration allows an analyst to quickly run the dig command on their Polarity server, enabling analysts to quickly see associated domains, IPs, and headers.
 Learn more
Learn more
Iris is a proprietary threat intelligence and investigation platform that combines enterprise-grade domain intelligence and risk scoring with industry-leading passive DNS data from Farsight Security and other top-tier providers. An intuitive web interface and API atop these data sources help security teams quickly and efficiently investigate potential cybercrime and cyberespionage. The Polarity DomainTools Iris integration allows Polarity to search Iris for risk information on Domains and Link back out to IRIS if there is associated information less than the count that you set below. More information on Iris: [https://www.domaintools.com/products/iris](https://www.domaintools.com/products/iris "https://www.domaintools.com/products/iris")
 Learn more
Learn more
The Polarity-Elasticsearch integration allows analysts to get real-time insights into any data contained within indexes in Elasticsearch, enabling analysts to work faster and more efficiently.
 Learn more
Learn more
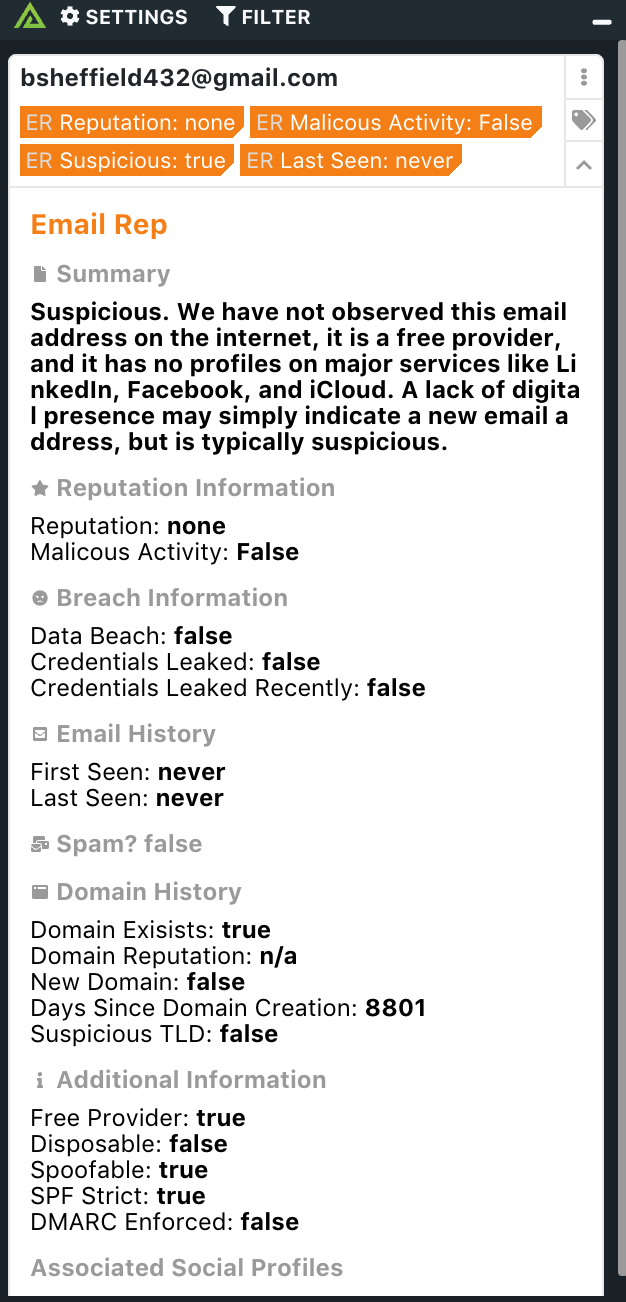
The Polarity - EmailRep integration returns reputation and history information about an email, allowing analysts to quickly understand if an email is something that is suspicious based on the EmailRep information.
 Learn more
Learn more
Security Operations Malware Analysis Incident Response Network and Infrastructure
Occasionally our users come across UNIX Epoch time, the representation of time as the number of seconds elapsed since January 1st, 1970. Polarity automatically converts Epoch time to a readable time.
Learn moreFarsight Security’s DNSDB™ is a Passive DNS historical database that provides a unique, fact-based, multifaceted view of the configuration of the global Internet infrastructure.
Learn moreThe FIR (Fast Incident Response) integration searches the FIR cybersecurity incident management platform for artifacts contained within cybersecurity incidents.
Learn moreThe Polarity FireEye Detection on Demand (DoD) integration allows Polarity to quickly identify malicious files contained within the FireEye platform. The FireEye DoD service only supports looking up MD5 hashes.
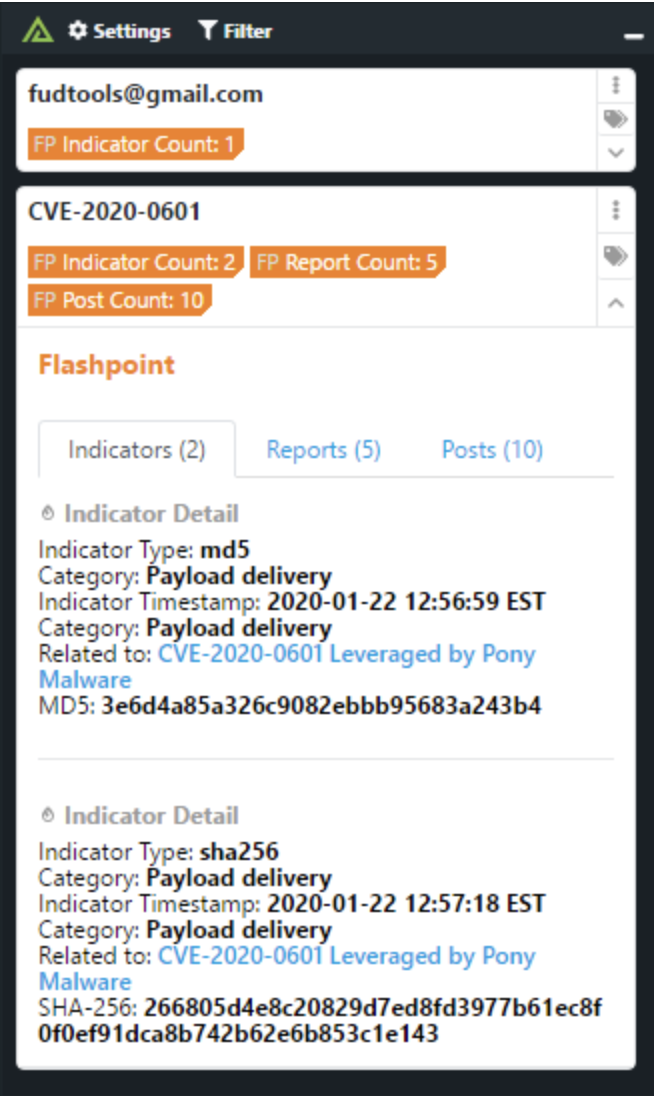
Learn moreThe Polarity - Flashpoint integration queries the indicators, reports, and forums endpoints in Flashpoint for IPs, domains, CVEs, and file hashes. These capabilities enable analysts to have a complete threat picture of indicators Flashpoint has information on, even enabling the analyst to quickly pivot to Flashpoint for further analysis.
 Learn more
Learn more
The Polarity Fortress integration allows for SHA-256 entity types to be enriched against the Fortress File Integrity Assurance (FIA) API.
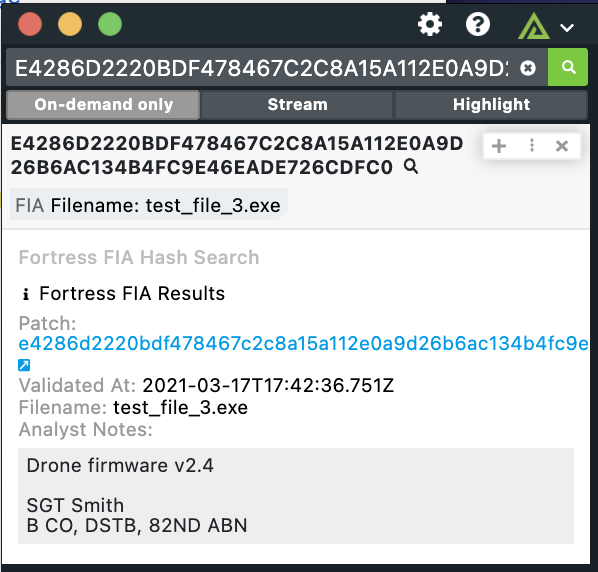 Learn more
Learn more
FullContact’s enrichment APIs let you transform partial identities into complete profiles to connect with prospects, capture audience insights, and enhance customer experiences.
Learn moreThe Polarity - Gigamon integration searches Gigamon for detection information as well as any associated DHCP, PDNS or Summary information.
Learn morePolarity's Google Compute Engine integration gives users the ability to lookup IP addresses and hostnames for VM instances in your Google Compute Engine infrastructure. The integration supports both internal and external IP lookups, and internal and custom hostnames. Internal hostnames must end in `.internal` and custom hostnames must end in a public suffix to be recognized.
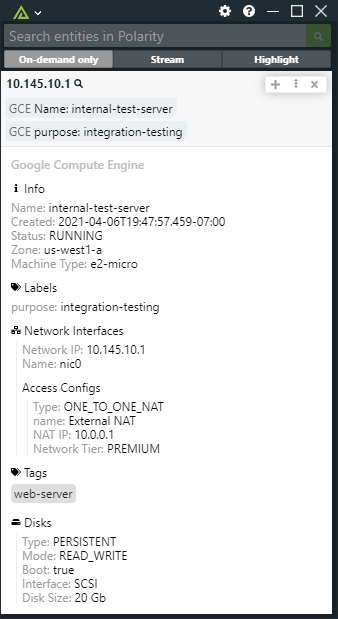 Learn more
Learn more
The Polarity Google Search Custom Search (CSE) allows the analyst to retrieve and display search results from Google Custom Search programmatically.
Learn moreThe Polarity - Google Maps integration enables analysts to geo-locate and pull back a map from google based on a lat-long or an address.
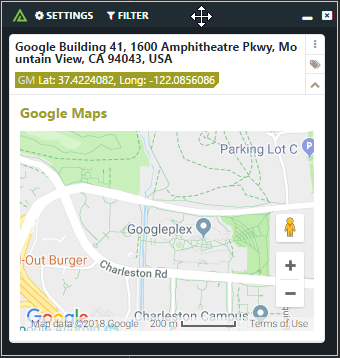 Learn more
Learn more
The Polarity - Google Translate integration enables analysts to quickly translate any foreign text to English with Polarity’s On-Demand mode. Allowing analysts to have a better understanding of what is being discussed in forums etc.
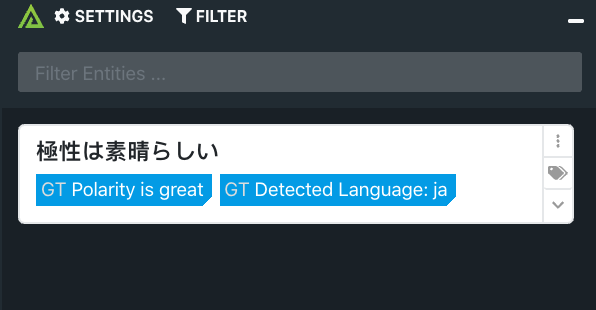 Learn more
Learn more
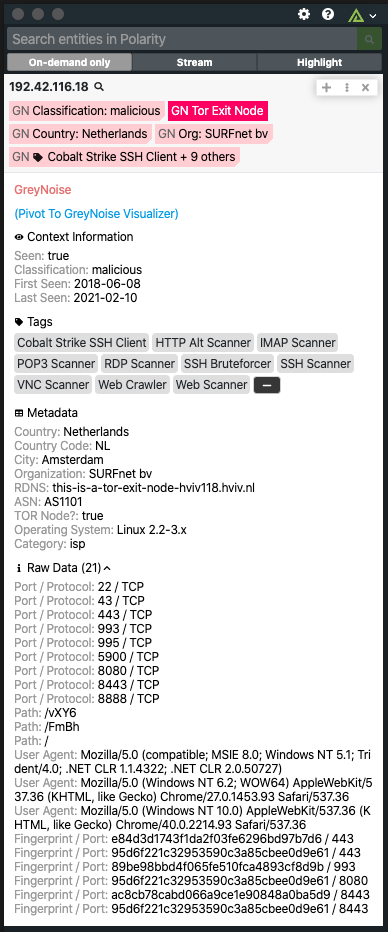
The Polarity - GreyNoise integration searches IPs in GreyNoise for internet scan and attack activity related to indicators on your screen. The scan and attack activity is then displayed via the Polarity Overlay Window, and we support the GreyNoise Community API out of the box if you do not already have an Enterpise API Key.
 Learn more
Learn more
The Polarity H-ISAC TAXII Feeds Integration retrieves Collections and Indicator Object data for Domains, URLs, Emails, IPs, and Hashes using H-ISAC's implementation of STIX 2.0 and TAXII 2.0.
 Learn more
Learn more
HackerOne is a hacker-powered security platform that provides unmatched cybersecurity speed, depth and breadth of coverage at a greater value. Polarity's HackerOne integration allows automated queries against HackerOne's API for all of your programs information relating to Scopes, Valued Vulnerabilities, Weaknesses, and Reports.
Learn moreCheck if you have an account that has been compromised in a data breach.
Learn moreThe Polarity host.io integration allows for domain entity types to be enriched against the host.io API enabling analysts to have instant context on a domains IP, backlinks, social sites and more. This is an on-demand only integration.
 Learn more
Learn more
Hybrid Analysis is a free malware analysis service for the community that detects and analyzes unknown threats using a unique Hybrid Analysis technology.
Learn moreIBM® QRadar® SIEM detects anomalies, uncovers advanced threats and removes false positives.
 Learn more
Learn more
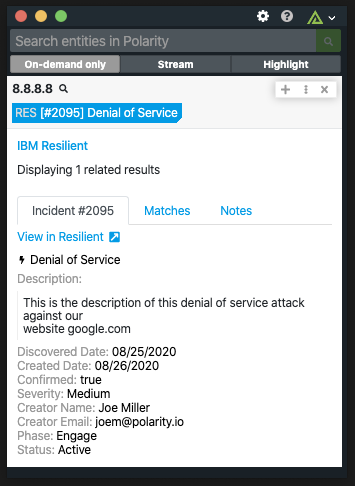
The Polarity - IBM Resilient integration searches the Resilient Incident Response Platform for incidents related to indicators on your screen. The integration can search across artifacts, incidents, tasks, and notes. Incident and tasks searches are full-text searches against all fields. Artifact searches are exact match searches against the artifact's value. Note searches are full-text searches against the content of the note. If a result is found, the integration will display information about the related incident. Incidents are deduplicated so that an incident is only shown a single time even if it has multiple matches. This allows analysts to quickly see when there are related tickets, enabling them to triage and close tickets faster and more efficiently.
 Learn more
Learn more
IBM X-Force Exchange is a cloud-based threat intelligence sharing platform enabling users to rapidly research the latest security threats, aggregate actionable intelligence and collaborate with peers.
Learn moreiDefense Security Intelligence Services provides security intelligence through the next generation IntelGraph platform that provides context, visualizations, searching, alerting and a robust RESTful API.
Learn moreThe Polarity Intel 471 integration allows Polarity to search the Intel 471 API to return information about various indicator types.
Learn moreThe ipinfo core API product returns geolocation, ASN, and hostname information for an IP address.
Learn moreSecurity Operations Incident Response Threat Hunting Pen Testing Threat Intelligence Open Source
The Polarity Malware Bazaar integration allows Polarity to quickly malicious file hashes contained within the Malware Bazaar platform.
Learn moreThe Polarity-Mandiant Threat Intelligence Integration allows analysts to have instant data awareness and recall on any intelligence from Mandiant dataset.
 Learn more
Learn more
Security Operations Threat Hunting Incident Response Pen Testing Threat Intelligence Open Source
The Polarity - Maxmind integration replicates the Geolocation database from Maxmind to enable analysts to have complete geo-location information for IP addresses, enabling analysts to quickly have an understanding of where an IP is located.
 Learn more
Learn more
Polarity's MeaDefender integration gives users access to potentially malicious file hash lookups against the MetaDefender OPSWAT REST API. MetaDefender is a cyber security platform for preventing and detecting cyber security threats on multiple data channels.
 Learn more
Learn more
The Polarity - MISP integration(s) enable a user to have an immediate understanding of their threat landscape when looking at indicators. Polarity has two integrations with MISP, 1 that enables a user to see the threat information on indicators and one to bulk submit indicators to MISP, enabling security analysts across teams to contribute and gain immediate awareness. Polarity - MISP - provides context around indicators in MISP. Polarity -MISP IOC Submission - enables analysts to bulk submit IOCs to MISP.
 Learn more
Learn more
The Polarity MISP integration allows Polarity to search your instance of MISP to return found domains, IPs, hashes, and emails. The integration also allows you to Create and Delete attributes (IOCs) in bulk from MISP. > **_NOTE_**: Attribute creation will create a new event containing all Attributes submitted.
 Learn more
Learn more
The Polarity MISP Warning Lists integration searches MISP hash, domain and IPv4 based warning lists and returns related list information.
Learn moreThe Polarity Nexpose Insight IDR Integration allows you to easily Query Emails, IP Addresses, Domains, and URLs in both Investigations, and Query Logs. You can also add Indicators to Threats, Close Investigations, and Assign Users to Investigations.
Learn moreThe Polarity OSINT Pivot integration allows an analyst to run an on-demand query against various indicator types to return a list of recommended OSINT resources to quickly pivot to.
Learn moreAutoFocus™ is a contextual threat intelligence service that accelerates analysis, correlation, and prevention workflows.
 Learn more
Learn more
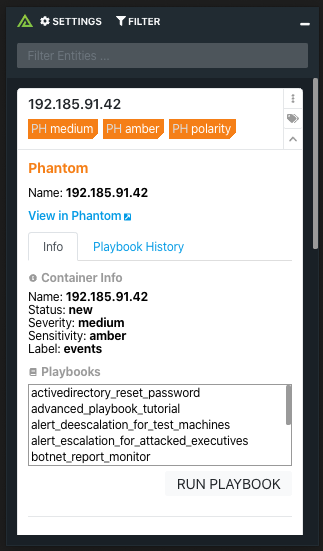
The Polarity - Phantom integration enables an analyst to have an immediate understanding of indicators in their Phantom artifacts and containers, while also providing a complete history of the playbooks and actions taken against the indicator, as well as enabling the analysts to run a playbook based on an indicator that either is not contained within an artifact or container or exists currently.
 Learn more
Learn more
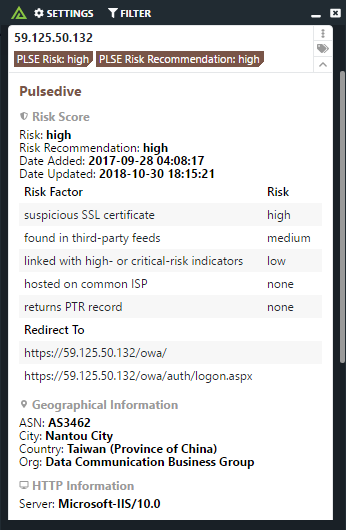
The Polarity - Pulsedive integration provides analysts real time community driven threat intelligence on ips and domains. Allowing analysts to have the vast risk knowledge that Pulsedive can provide in any workflow they are using.
 Learn more
Learn more
The Polarity - Recorded Future searches the Recorded Future API for threat information on associated indicators. Allowing analysts to have the power of Recorded Future's vast threat intelligence no matter what application they are looking at, enabling better data awareness and recall.
 Learn more
Learn more
Open-source project management application. There is also the Redmine Issue Creator integration, which allows for users to create a ticket in Redmine.
 Learn more
Learn more
ReversingLabs delivers industry-leading threat detection and analysis solutions that address the latest generation of cyber attacks.
 Learn more
Learn more
Security Operations Incident Response Malware Analysis Network and Infrastructure
The A1000 Malware Analysis Platform supports advanced hunting and investigations through the TitaniumCore high-speed automated static analysis engine.
 Learn more
Learn more
The Polarity RIPEstat integration allows Polarity to return all announced prefixes for a given ASN via the RIPEstat Data API.
Learn morePolarity - RiskIQ integration allows Polarity to search RiskIQ Security Intelligence Services (SIS API) to return threat information on IP's, Domains and URL's.
 Learn more
Learn more
The Polarity Sandbox integrations uses the Google search API to search malware on different internet hosted sandboxes, to provide more information on the malware hashes.
 Learn more
Learn more
The Polarity Securonix integration allows Polarity to search Securonix API to return User Violation information on Emails, Domains and IP's.
Learn morePolarity's ServiceNow Security Incident Response (SIR) Integration allows the lookup of ServiceNow security incidents (e.g. SIR00000012), and Observables including IP addresses, CVE's, web domains, file hashes and e-mail addresses against your instance of ServiceNow.
 Learn more
Learn more
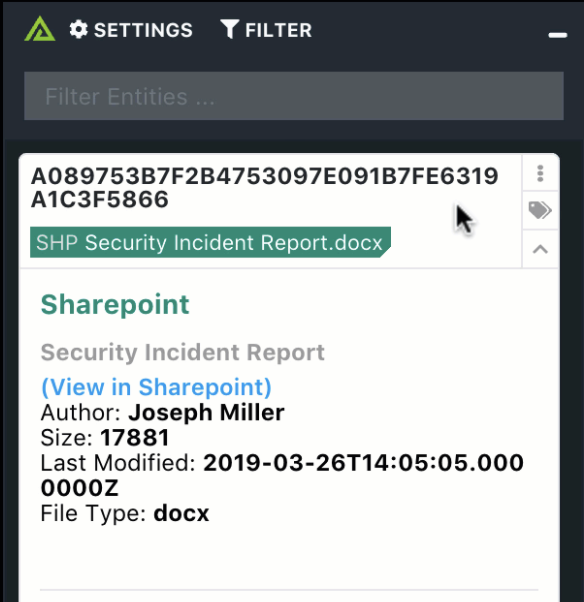
The Polarity Sharepoint integration allows freeform text searching for IPs, hashes, and domains in your Sharepoint instance and retrieves related documents.
 Learn more
Learn more
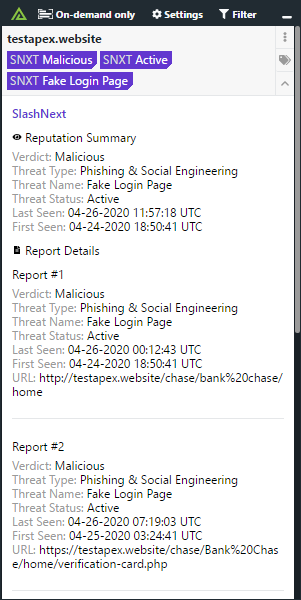
The Polarity SlashNext integration allows Polarity users to leverage SlashNext's On-demand Threat Intelligence (OTI) for the analysis of suspicious IPv4 addresses and domains.
 Learn more
Learn more
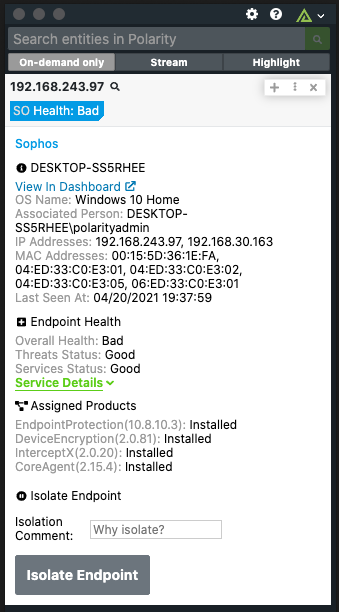
The Polarity Sophos integration allows Polarity to search Sophos to return found domains, urls, IPs, and SHA256 hashes. The integration also allows you to Isolated found endpoints, and add SHA256 hashes to your Block and Allow Lists.
 Learn more
Learn more
The Polarity - Splunk integration enables you to quickly search any index in your Splunk Enterprise or Splunk Cloud instances. Enabling you to have complete awareness of any indicators that matter to you and your teams.
 Learn more
Learn more
Sumo Logic, Inc. is a cloud-based machine data analytics company focusing on security, operations and BI use cases. It provides log management and analytics services that leverage machine-generated big data to deliver real-time IT insights. This integration will run the provided search query and return the first 10 results.
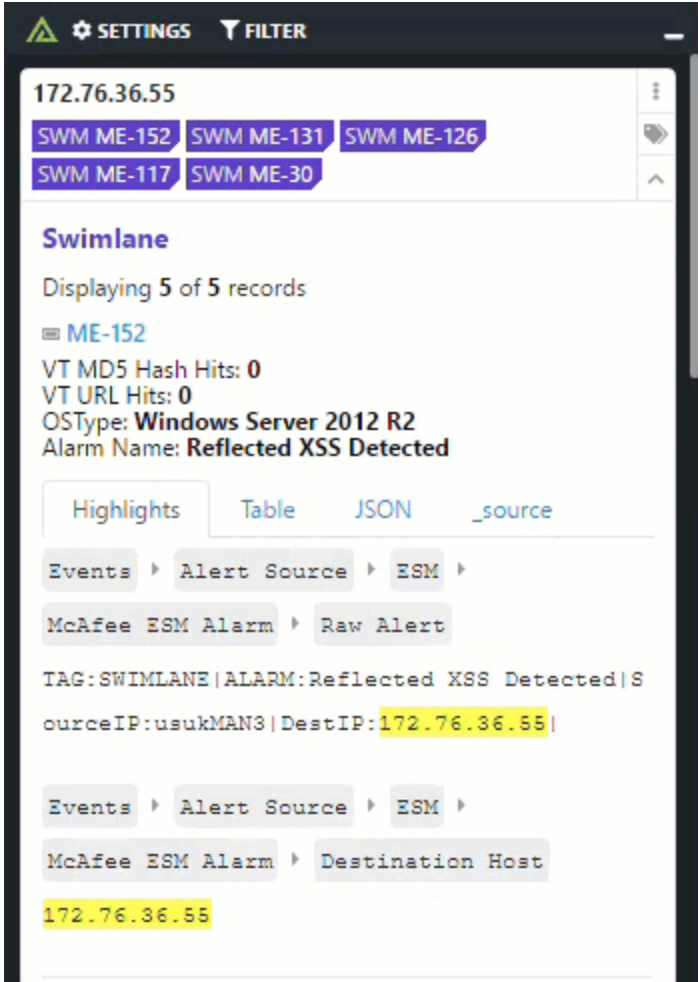
Learn moreSwimlane automates manual processes and operational workflows by delivering powerful, consolidated analytics, real-time dashboards, and reporting from across your security infrastructure.
 Learn more
Learn more
The Polarity - TheHive integration allows Polarity to search TheHive's Search API to return threat information on IP's, Domains and URL's.
 Learn more
Learn more
Security Operations Incident Response Threat Hunting Threat Intelligence Security and Incident Response
The Polarity - ThreatConnect integration(s) enable a user to have an immediate understanding of their threat landscape when looking at indicators. Polarity has two integrations with ThreatConnect, 1 that enables a user to see the threat information on indicators and one to bulk submit indicators to ThreatConnect, enabling security analysts across teams to contribute and gain immediate awareness. Polarity - ThreatConnect - provides context around indicators in ThreatConnect and enables users to link out to Playbooks and run from the ThreatConnect Ui. Polarity -ThreatConnect IOC Submission - enables analysts to bulk submit IOCs to Threatstream.
 Learn more
Learn more
The Polarity ThreatConnect integration allows Polarity to search your instance of ThreatConnect to return found domains, IPs, hashes, and emails. The integration also allows you to Create and Delete Indicators (IOCs) in bulk from ThreatConnect.
 Learn more
Learn more
Security Operations Incident Response Threat Hunting Threat Intelligence Security and Incident Response
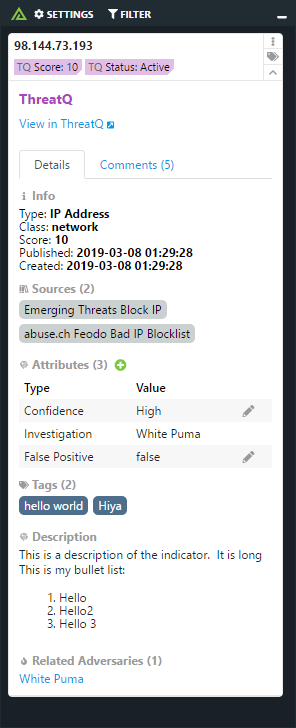
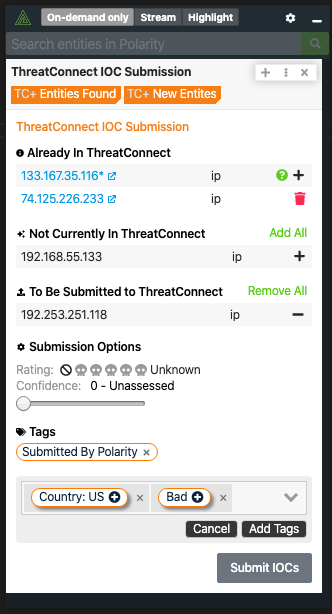
The Polarity - ThreatQuotient integration(s) enable a user to have an immediate understanding of their threat landscape when looking at indicators. Polarity has two integrations with ThreatQuotient, one that enables a user to see the threat information on indicators and one to bulk submit indicators to ThreatQuotient, enabling security analysts across teams to contribute and gain immediate awareness. Polarity - ThreatQuotient - provides context around indicators in ThreatQuotient. Polarity -ThreatQuotient IOC Submission - enables analysts to bulk submit IOCs to Threatstream.
 Learn more
Learn more
The Polarity ThreatQuotient integration allows Polarity to search your instance of ThreatQuotient to return found domains, IPs, hashes, and emails. The integration also allows you to Create and Delete Indicators (IOCs) in bulk from ThreatQuotient.
 Learn more
Learn more
The Polarity ThreatStream IOC Submission integration gives users allows users to submit indicators of compromise to Anomali's ThreatStream platform.
 Learn more
Learn more
The Polarity TrapX integration allows Polarity to search the TrapX DeceptionGrid API to return event information on IP addresses.
Learn moreSecurity Operations Incident Response Threat Hunting Threat Intelligence Security and Incident Response
The Polarity TruSTAR integration allows Polarity to search the TruSTAR API to return information about various indicator types.
 Learn more
Learn more
The Polarity Twitter integration uses the Google search API to search for twitter for related tweets around your search parameters.
 Learn more
Learn more
The Polarity URL Pivot integration allows an analyst to run an on-demand query against an IP, hash, domain or email to return a list of queries that they can then execute in their SIEM or any other URL users want to search.
Learn moreThe Polarity USCert integration uses the Google search API to search for indicators all throughout USCerts website.
 Learn more
Learn more
The Polarity-VirusTotal integration provides instant awareness on hashes from VirusTotals vast database on malicious indicators. Enabling analysts to triage file hashes and IPs to see if there are any known viruses, trojans etc that have been associated with them.
 Learn more
Learn more
Displays information about Windows security audit events
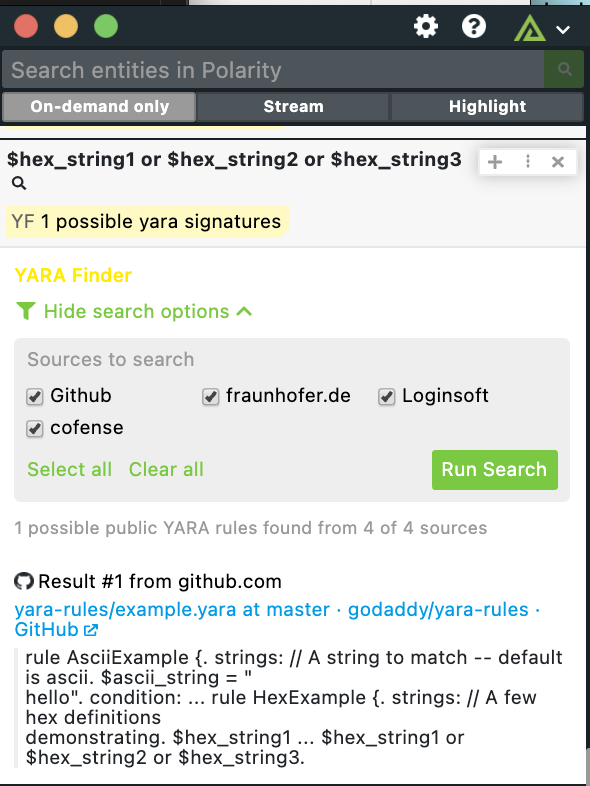
Learn moreThe Polarity Yara finder uses the Google search API to search for publicly available Yara Signatures from the following websites. * Github.com * Cofense * Fraynhofer.de * Loginsoft
 Learn more
Learn more
Zendesk is a customer service and engagement platform. The Polarity Zendesk integration displays relevant ticket information based on email addresses and domains.
Learn more