Configuring IBM Resilient
This integration requires you to complete a few extra steps in order to use it.
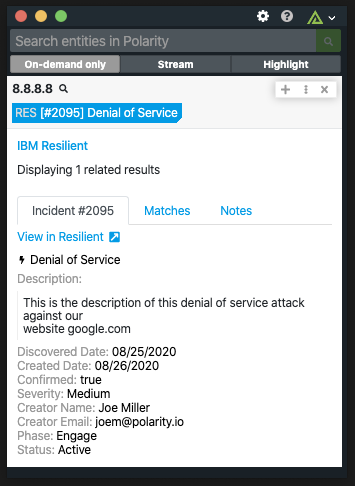
In order to use the Polarity - IBM Resilient integration, configuration of the integration is required.
Entity Types: Ips, domains, emails, file hashes
Configuration Options
Resilient Url - The base url used to access the instance of IBM Resilient. This is the same url that analysts will go to when logging into Resilient. This option is typically set by a Polarity admin for all Polarity users to utilize.
Resilient Username - Analysts username that is needed to log into IBM Resilient. This option may be set by a Polarity admin with a service account.
Resilient API Key - API Key used to connect to Resilient. Will need to be generated by a Resilient administrator. This option will only work if you do not have basic authentication turned on.
Resilient Password - Analysts password that is needed to log into IBM Resilient. This option may be set by a Polarity admin with a service account.
Types to Search - This option allows analysts what portions of IBM Resilient they want to Polarity integration to search. The options include: incidents, notes, tasks and artifacts. The analysts can select all or just one of the options. This option is typically set by a Polarity admin for all Polarity users to utilize.
**Ignore List or Ignore Regex **- Resilient Integration enables the ability to set a regex to match domains or ips to be ignored or add in a comma separated list, so the integration will never look them up in Flashpoint. This is typically used for sensitive information or company domains.