Extend the Power of Polarity
Polarity is an overlay on top of all your existing workflows and tools. You can also build on top of Polarity to extend the power of the platform. Explore available open source projects here:


The Polarity BinaryEdgeintegration allows for enrichment of IP's, Domains and E-mail addresses. Free accounts are limited to 250 queries per month. If you are using a free, account we highly recommend running this integration as On-Demand Only. Register for a free account at the URL below: [https://app.binaryedge.io/sign-up](https://app.binaryedge.io/sign-up "https://app.binaryedge.io/sign-up")
 Learn more
Learn more
The Polarity Censys integration allows the Polarity user to quickly perform research against the three Censys maintained datasets collected via daily ZMap scans of the Internet and by synchronizing with public certificate transparency logs.
 Learn more
Learn more
Security Operations Incident Response Threat Hunting Pen Testing Network Engineering SIEM
Polarity's Chronicle Backstory integration allows automated queries to the Events, Assets, and IOC Details endpoints in Chronicle Backstory's API from the Polarity overlay window.
Learn moreThe Polarity CRXcavator integration is an on-demand integration which provides risk information about third-party Chrome extensions based on the extension ID. The extension ID is a 32 character string made up of alphabetical letters. The integration will return risk information for the most recent version of the extension as well as information for the version of the extension with the maximum risk, and information for the version of the extension with the minimum risk. Finally, a risk history table is displayed which lets an analyst view the change in risk over time for the integration.
 Learn more
Learn more
The Polarity Exploit finder uses the Google search API to search for publicly available exploits from the following websites. * Exploit-db.com * Github.com * PacketStormSecurity.com * 0day.today * Vulnerability-Lab.com * CXSecurity.com * SecurityFocus.com * Rapid7.com * SecuriTeam.com * exploit.kitploit.com
 Learn more
Learn more
The Polarity Google Search Custom Search (CSE) allows the analyst to retrieve and display search results from Google Custom Search programmatically.
Learn moreSecurity Operations Incident Response Threat Hunting Pen Testing Threat Intelligence Open Source
Security Operations Threat Hunting Incident Response Pen Testing Threat Intelligence Open Source
The Polarity - Maxmind integration replicates the Geolocation database from Maxmind to enable analysts to have complete geo-location information for IP addresses, enabling analysts to quickly have an understanding of where an IP is located.
 Learn more
Learn more
The Polarity OSINT Pivot integration allows an analyst to run an on-demand query against various indicator types to return a list of recommended OSINT resources to quickly pivot to.
Learn moreDecode URLs which have been rewritten by TAP to their original, target URL. For more information about the Proofpoint URL Decoder API please see [https://help.proofpoint.com/Threat_Insight_Dashboard/API_Documentation/URL_Decoder_API](https://help.proofpoint.com/Threat_Insight_Dashboard/API_Documentation/URL_Decoder_API "https://help.proofpoint.com/Threat_Insight_Dashboard/API_Documentation/URL_Decoder_API")
Learn moreThe Polarity Sandbox integrations uses the Google search API to search malware on different internet hosted sandboxes, to provide more information on the malware hashes.
 Learn more
Learn more
The Polarity - Shodan integration provides immediate awareness to Shodan’s vast Internet of Things search engine. Enabling analysts to quickly triage the location, associated domains and headers for an IP.
 Learn more
Learn more
The Polarity - VulDB integration provides immediate awareness of vulnerability information related to CVE’s and Microsoft Security Bulletins. Enabling analysts to have the community-driven vulnerability information immediately available whenever there is a CVE or KB ID on their screen.
 Learn more
Learn more
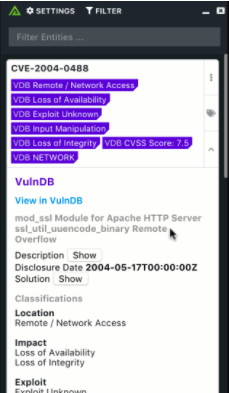
With Polarity’s VulnDB integration, you have ready access to the vast intelligence that VulnDB provides anytime there is a CVE on your screen. No matter what you are looking at, whether it’s the output of a vulnerability scan or a PDF with the latest threat information, you will have the power of VulnDB’s vulnerability data overlaid on your screen. The integration also provides a link directly to VulnDB’s SaaS Portal, ensuring you have full access to VulnDB’s comprehensive vulnerability intelligence right when it’s needed most.
 Learn more
Learn more
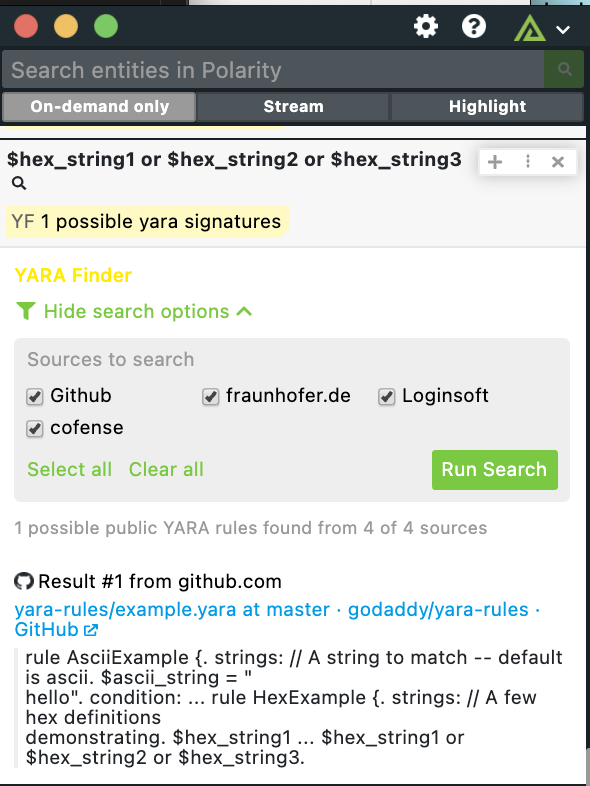
The Polarity Yara finder uses the Google search API to search for publicly available Yara Signatures from the following websites. * Github.com * Cofense * Fraynhofer.de * Loginsoft
 Learn more
Learn more
Social Media Searcher
Pen Testing Threat Hunting
Learn more
The Polarity Social Media Searcher uses the google search API to pass through programmatically search if there are any known social media accounts on any of the following websites. * facebook.com * twitter.com * instagram.com * tiktok.com * reddit.com * parler.com * linkedin.com
Learn more