Who needs another dashboard?
Work never happens in one place and tools are continuously changing. Instead of teams searching in multiple sources for information, Polarity augments data and information from your existing applications.
Without Polarity
Multi-source searching from different tools

With Polarity
Your data brought to you in real-time
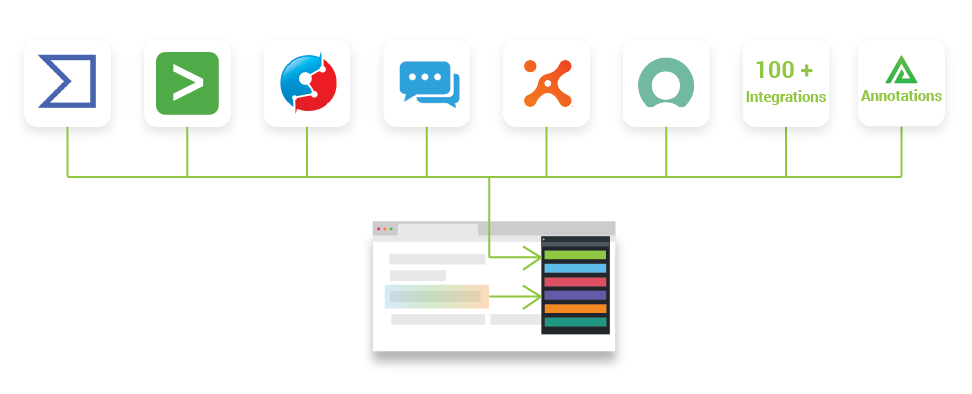
How it works
Polarity augments data from two places:
-

Integrations
With over 120 open source integrations , leverage data from your existing tools, or quickly build you own integration.
View All Integrations -

Annotations
From any application, you can annotate any string with information worth sharing or remembering. This could be notes on a customer, evidence from an investigation, or intelligence on a threat.

Highlight Data You Care About
On every log you triage, event you view, index you open, playbook you analyze, malware you reverse engineer, or network you search.
Get the context needed to do your job with thoroughness and speed.

The best hackers know the right time to automate a task to scale their capability.
Without Polarity
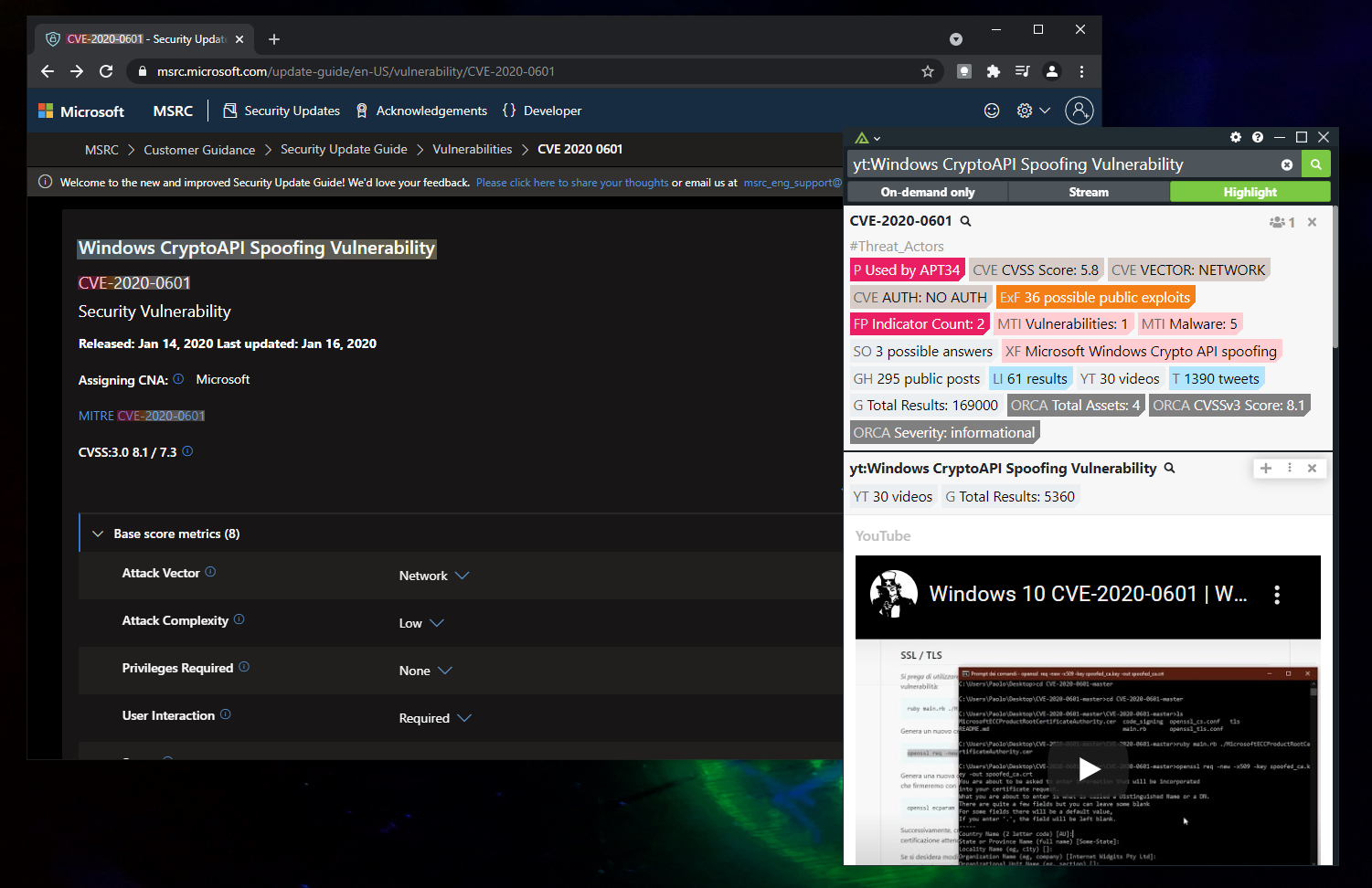
With Polarity, if you are looking at a vulnerability, Polarity can kick off the research for you by automatically searching and finding public/commercial exploit code with YouTube videos on exploitation steps.
Polarity enables you to automate your research to reduce busy work and better simulate the adversary.
Know what ports are open before the port scan.

It can pull back intel reports on adversaries that are exploiting the same vulnerability with relevant dark web chatter.

And if a purple team exercise, even pull back details on the affected assets.

Trusted by 6 of the top 100 US companies, and thousands of analysts globally
This is one of the few tools that I recommend outright based on a demo alone. The capability is awesome.
Andy Piazza
Polarity enabled our incident response team to quickly draw on historic intelligence which furthered their ability to respond effectively to observed events
CIO, Leading Media and Internet Company
Winner of two awards: Editors Choice Infosec Startup of the Year, and Best Product - Memory Augmentation
Cyber Defense Magazine
Polarity is a force- multiplier for our security team whether its threat hunting or another discipline. With Polarity in Highlight or On-demand mode we have confidence that all of our most valuable information is delivered to our analysts, cross referenced against multiple sources, and is acted upon by the right people at the right time.
Michael Francess
Manager, Cyber Security Advanced Threat
Our investment in Polarity led to an annual ROI of nearly 200% based on just its initial use cases. Since purchase, we continue to find ways to use Polarity to increase the speed and thoroughness of the team.
Cybersecurity Manager
Leading Financial Service Company
...really haven’t stopped using it since you showed me it, great little tool.
Robert Gasior
CIRT Lead EMEA
You guys continue to set the bar for what Customer Support should be
SOC Manager
Verizon Media